Lightning Network Risks & Challenges
While still in early development, the Lightning Network effectively scales Bitcoin transactions but faces challenges like liquidity constraints, centralization, and regulatory hurdles.
•
8 min read

The Lightning Network (LN) is an evolving technology, meaning that unexpected technical issues, bugs, or vulnerabilities may pose risks to its security and stability. Additionally, there are several well-known challenges that LN must overcome to achieve global adoption.
Here are some of the primary risks and challenges associated with LN:
Technological risks and challenges
Liquidity Constraints
In the context of the Lightning Network, liquidity refers to the amount of Bitcoin committed to payment channels. Liquidity is essential for routing payments as it directly impacts the user experience: if certain channels don't have enough liquidity, it may result in suboptimal routing or even payment failures. This is particularly problematic for businesses or individuals who want to accept LN payments.
- If a user has no outbound liquidity, they can’t make payments, while a user lacking inbound liquidity can’t receive BTC through Lightning.
- When outbound liquidity in forwarding channels is limited, users often have to divide their payments over several routes, especially for amounts larger than small micropayments. On the other hand, channels with enough inbound liquidity to handle large payments are rare.
- Although payment failures on the LN are not very common, they can still occur. A report by River indicated that in August 2023, the success rate of Lightning payments on its platform was 99.7%, based on 308,000 transactions. Payment failures happened when a route with sufficient liquidity to complete the transfer could not be found.
Stroom mitigates these risks by running a well-connected and well-funded Lightning node. We apply custom algorithms to manage channels and liquidity in order to be a capital-efficient and reliable router.
Channel Management Issues
In a payment channel, funds move from one side to the other. If all funds end up on one side of the channel, it can no longer be used for transactions in the opposite direction, requiring rebalancing. Rebalancing, in turn, is subject to fees and may take time.
Opening and closing channels involve on-chain transactions, which can be costly and time-consuming.
Lightning Network infrastructure requires constant support, which might be challenging for non-professional teams. It's important to monitor channels and shut them down if they're not actively being used for routing, as this can lead to inefficient use of liquidity.
Liquidity imbalances in channels can also impact the ability to find suitable payment routes.
Stroom mitigates those issues by removing the technical burden of self-hosting a routing LN node and the need to deposit BTC in LN while also enabling users to participate in liquid staking within EVM-compatible DeFi ecosystems.
Centralization concerns
Lightning Network’s current design means that nodes need to be online to facilitate transactions. If a significant portion of nodes goes offline, it can impact the user experience, undermining the network's overall reliability and trust in the system.
This, for example, can happen if the majority of the nodes rely on the same cloud provider. As of July 2024, nearly a half all LN nodes are hosted by major centralized cloud service providers, with amazon Web Services (AWS) covering more than 30% of all nodes, and Google Cloud being home to approximately 18.5% of nodes.
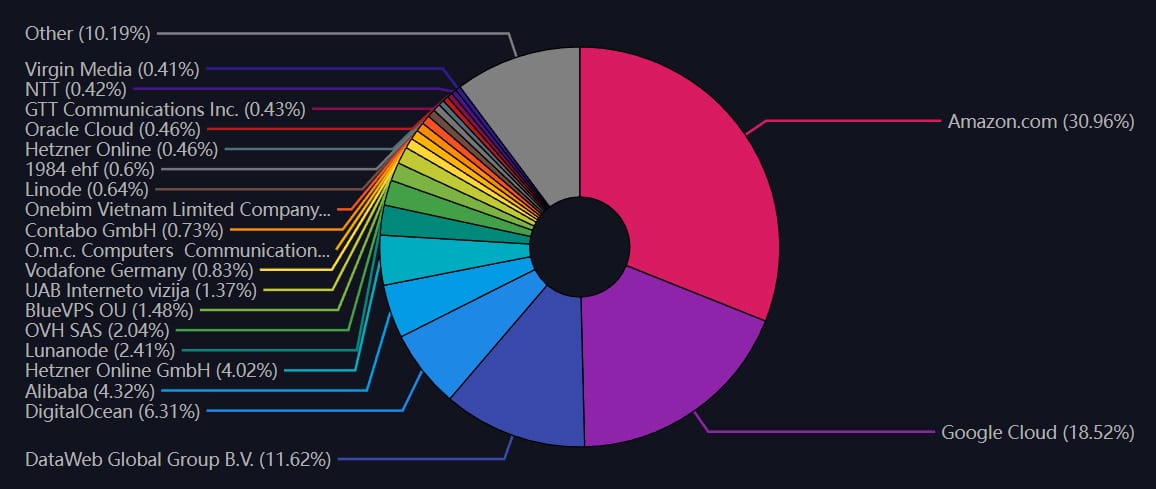
This reliance on centralized cloud services is primarily to ensure high uptime and reliability for the nodes, as both parties in a Lightning Network transaction need to be online for successful transaction execution. This approach, however, indicates a worrying degree of centralization at the infrastructure level, which contradicts the decentralized ethos of blockchain technology and could lead to points of failure if these services face downtime.
Centralizing a significant portion of the network’s infrastructure in the hands of a few cloud service providers could make the Lightning Network more vulnerable to targeted attacks. If these providers suffer from security breaches, a large portion of the network could be compromised simultaneously.
Additionally, the Lightning Network could become centralized around a few major nodes, which could route a significant portion of all transactions. This centralization could lead to issues like censorship, increased fees, or single points of failure.
Fully mitigating these challenges may be a daunting task, and during its initial phase (Phase 1), the Stroom project will operate with a centralized small group of Lightning Network node operators. Phase 2, however, will see Stroom undergo a transition towards a decentralized autonomous organization (DAO)-governed LN node management approach with a bigger number of independent LN routers.
Security and Privacy Concerns
The security of funds in Lightning Network channels is crucial. Users need to be vigilant about potential attacks or vulnerabilities.
These include, but are not limited to:
- Hot Wallet Vulnerability: Lightning Network nodes need to keep their funds in hot wallets to facilitate instant transactions. This exposes them to potential security threats, such as hacking attempts.
- Channel Breaches: If a participant in a payment channel tries to cheat by broadcasting an outdated channel state, it may lead to the loss of funds for the counterparty. To address this issue, the Lightning Network utilizes Watchtower services that monitor specific LN channels to prevent fraud. Watchtowers are an essential component of the LN's security infrastructure, allowing users to outsource the monitoring of their channels to a third party. Watchtowers continuously surveil the blockchain for any potential malicious activity, such as outdated channel closes, and issue justice transactions to penalize dishonest actors. Still, this mechanism doesn't eliminate the risk entirely. The security of the network relies on these protocols being correctly implemented and adhered to by all participants.
- Channel Closure and Settlement Risks: When a channel is closed, the final state of the channel is broadcasted to the Bitcoin blockchain. If there's a dispute about the state of the channel, or if one party tries to close the channel dishonestly, there might be a risk of funds loss.
- Replacement Cycling Attacks: A vulnerability called "replacement cycling attacks" was identified in the Lightning Network, which could potentially jeopardize the security of funds and allow sophisticated attackers to execute a "transaction-relay jamming attack." This vulnerability was disclosed to Lightning developers, and mitigation measures have been deployed across major LN implementations. However, there are concerns about the effectiveness of these mitigations against more advanced forms of attack. The more fundamental solution to this problem is being researched and will be released as a Bitcoin soft fork soon.
- Man-in-the-Middle Attacks: Hashed Timelock Contracts (HTLCs) utilized by LN require that all nodes in the route use the same payment hash. If an attacker controls more than one node in a payment route, they could potentially correlate payments to senders and receivers by comparing the payment hash. This risk is especially significant for mobile wallets, which often have a single connection to a Lightning Service Provider (LSP) and are mostly offline. This risk is mitigated by introducing Taproot channels and a more advanced version of time-lock contracts - PTLC.
- Third-Party Services: The privacy of Bitcoin payments on the Lightning Network relies on the parties involved in the transactions and their adherence to privacy principles. If users are not aware of the privacy risks or do not take appropriate measures, their privacy may be compromised. However, such tracking is super hard to do due to the embedded onion routing in the LN protocol.
Stroom mitigates some of those issues by introducing LN Hubs, which require all routing LN nodes within the system to adhere to the Stroom protocol. These nodes will not possess access to the funds held within their respective channels, and any action that modifies the channel's state will require authorization from validating nodes.
Adding a layer of security, a federation of validating nodes independently checking each event that requires approval without relying on other nodes. A minimum of 2/3 + 1 votes from the validating nodes is required to finalize an approval.
Additionally, the introduction of an inherent Stroom Watchtower functionality will allow the system to automatically monitor the state of the channels. If an LN node fails to comply with the rules established by the federation of validating nodes, the latter will take action by closing all channels associated with that non-compliant LN node and removing it from the system.
Stroom adheres to all LN channel management best practices while actively monitoring the Bitcoin developers' mailing list and engaging with developers to stay updated about new upgrades.
Regulatory risks and challenges
There's an ongoing debate about how to classify cryptocurrencies. Are they currencies, commodities, securities, or something else entirely? This classification affects how they and related technologies like the Lightning Network are regulated.
Different jurisdictions have varying approaches to cryptocurrency regulation. Some are more open and have clear guidelines, while others are more restrictive or have not yet developed specific policies. This patchwork of regulations can make it challenging for Lightning Network services to operate globally, impacting their development and adoption.
While it's still largely unclear how regulatory frameworks may apply to decentralized networks like the Lightning Network, there’s a possibility that operators of Lightning nodes, especially those that route significant amounts of transactions, might face regulatory scrutiny regarding AML and KYC compliance.
Notably, while LN nodes are not considered money transmitters, according to the FinCEN guidance, some argue that they could be interpreted as money services businesses (money transmitters) depending on the interpretation of state regulations.
On the other hand, there is an argument that Lightning Network nodes should not necessarily be subjected to Money Transmitter Rules (MTR). This perspective is based on the operational nature of Lightning Network nodes, which primarily route transactions along the network rather than holding or transferring funds as a typical money transmitter would.
Taxes are another thing to keep in mind. Tax authorities in various jurisdictions are still figuring out how to treat transactions on networks like the Lightning Network. Issues include how to track gains, losses, and income from cryptocurrency transactions for tax purposes.
As with any emerging technology, there's a lag between technological development and regulation. How regulators choose to catch up with technologies like the Lightning Network could significantly impact its growth and user adoption.
Lightning Network Adoption
The widespread adoption of the Lightning Network as a payment system requires acceptance by a large number of merchants and a high level of user awareness. Merchant adoption is currently limited due to complexities in integrating the LN into existing payment systems and concerns about Bitcoin's price volatility and regulatory uncertainties. On the other hand, there's also a need to increase user awareness about the benefits and ease of using LN payments.
User Experience Challenges
Setting up and using Lightning channels can be challenging for non-technical users. Enhancing user interfaces and streamlining the onboarding process are crucial for broader adoption.
The separation between Layer 1 (Bitcoin) and Layer 2 (Lightning) adds complexity to payment flows. Moving Bitcoin between these layers can be time-consuming and adds to the complexity of managing payments.
Economic Challenges
Aligning economic incentives for users and node operators to participate in the Lightning Network is an ongoing challenge. Ensuring that participants are adequately compensated for providing liquidity and routing services is essential.
Another thing to take into account is the need to pre-deploy liquidity in channels. Users must ensure their nodes have sufficient liquidity in the correct channels to support payments, which can be complex and often confusing.
Stroom mitigates those issues by enabling users to earn revenue without the need to lock up their BTC or maintain their own LN node infrastructure. To participate, users can deposit their BTC into the Stroom treasury and, in return, receive wrapped tokens issued on EVM-based blockchains. The Stroom DAO then utilizes the staked liquidity to engage in Lightning Network channels, where it generates yield through the fees collected by Stroom's Lightning Network routing nodes.
*****
We trust you've found this article helpful. To learn more about Stroom, access detailed information about our technology, or explore how you can join the ecosystem, visit the following resources:
Official website: https://stroom.network/
Whitepaper: https://stroom.network/Primer.pdf
Twitter (X): https://x.com/StroomNetwork
Discord: https://discord.gg/DZ53WjDXz9
Telegram: https://t.me/stroomnetwork

Stroom DAO
View our other posts

Bitcoin Without Borders: Unlocking Bitcoin's Multi-Chain Potential
Since the birthday of the first Bitcoin block on January 3, 2009, a new era of financial assets has begun - the cryptocurrency era. Unmatched security, permissionlessness, and decentralization cemented Bitcoin'
Stroom DAO

Lightning Network in 2025: Bitcoin’s Transformation into Everyday Money
Bitcoin’s Lightning Network is transforming from an experiment into a global payment system, making everyday transactions faster and cheaper.
Stroom DAO

Lightning Network: Celebrating 9 Years of Innovation
The Lightning Network whitepaper was unveiled on January 14, 2016, introducing a transformative layer atop Bitcoin for instant, scalable transactions.
Stroom DAO